The End of the “Bad Grammar” Scam: How AI-Powered Phishing is Targeted and Perfect
January 6, 2026
Beyond Backups: Protecting Your Houston Business from Ransomware 3.0
January 8, 2026By the Team at Krypto IT | Cybersecurity Experts Serving Houston SMBs
For years, Business Email Compromise (BEC) followed a predictable script. A hacker would gain access to a corporate email account or spoof a domain to send a message that looked like it came from the CEO or a trusted vendor. The goal was simple: trick an employee into wiring money or changing payroll details. It was a text-based game of deception that relied on urgency and authority.
But as we enter 2026, the script has been completely rewritten. We are now in the era of Deepfake BEC.
Cybercriminals are no longer limited to the written word. They are using generative AI to create “multimodal” attacks that include hyper-realistic video and audio components. At Krypto IT, we are seeing a shift where a phishing email is just the “hook,” followed by a deepfake “proof” that is nearly impossible for the untrained eye to catch. Here is why Deepfake BEC is the most dangerous threat facing Houston’s SMB landscape today.
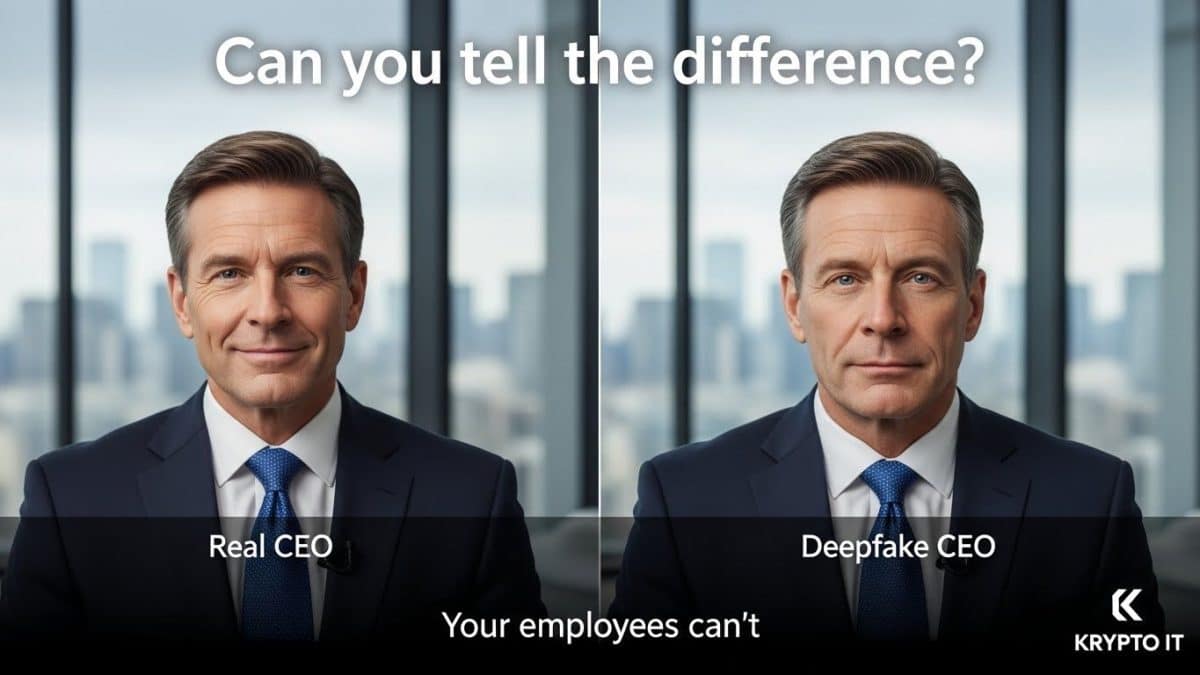
1. Beyond the Text: The “Multimodal” Attack
In a traditional BEC attack, a suspicious employee might hesitate and think, “This doesn’t quite sound like my boss.” To counter this, hackers are now including “proof” in the form of deepfake media.
Imagine an employee receives an email from their CFO regarding a confidential merger. The employee is skeptical. Moments later, they receive a video message via a collaboration tool like Teams or Slack. In the video, the “CFO” is sitting in what looks like their actual office, speaking with their actual voice, and confirming the instructions in the email.
This isn’t science fiction; it is happening now. By combining text-based phishing with deepfake video or audio, hackers create a “closed loop” of deception that bypasses the natural skepticism of even the most diligent employees.
2. Why Houston SMBs are the Primary Target
While global enterprises are frequently in the news, Houston’s mid-market businesses—particularly those in the energy, construction, and legal sectors—are the “sweet spot” for Deepfake BEC.
Why? Because these businesses often handle high-value transactions (such as real estate closings or vendor payments for industrial equipment) but may lack the enterprise-grade “Deepfake Detection” tools found in Fortune 500 companies.
Hackers use a simple formula to determine their targets:
By targeting a Houston real estate firm or a logistics company, the hacker finds a high “Value of the Prize” with a much lower “Complexity of Defense.”
3. The Anatomy of a Deepfake “Identity Theft”
How do they do it? The process is surprisingly accessible for criminals in 2026:
- Scraping: The hacker finds a video of your CEO speaking at a Houston Chamber of Commerce event or a “Company Culture” video on your website.
- Training: They feed that video into a Generative Adversarial Network (GAN). The AI learns the CEO’s facial movements, their blinking patterns, and the cadence of their speech.
- Deployment: The hacker writes a script and uses the AI to “render” a new video or audio clip.
This “identity theft” is far more damaging than a stolen password. A password can be changed; your face and voice cannot.
4. The Psychological “Trust Trap”
The reason Deepfake BEC is so successful is that humans are hardwired to trust our eyes and ears. We have been trained for decades that “seeing is believing.” When we see a familiar face on a screen, our brain’s critical thinking centers often take a back seat to our social instincts.
Hackers exploit this “Trust Trap.” They create scenarios of extreme urgency—a missed payment that threatens a major project or a “confidential” opportunity that requires immediate action. The combination of visual “proof” and emotional pressure is a devastatingly effective weapon.
How Krypto IT Protects Your Business
When technology can perfectly mimic humanity, how do you defend your company? At Krypto IT, we move beyond “software-only” solutions and implement a Strategic Defense Framework:
- Out-of-Band Verification (OOBV): We help you implement mandatory policies where any financial transaction above a certain threshold must be verified through a secondary, pre-approved channel (like a direct phone call to a known number), regardless of how “real” the video looks.
- Deepfake Awareness Training: We educate your staff on the “uncanny valley” markers of deepfakes—such as unnatural eye movements, blurring around the mouth, or inconsistent lighting.
- Multi-Factor Everything: We ensure that no single person has the “keys to the kingdom.” By implementing multi-sig (multiple signature) requirements for large transfers, we make it impossible for a single deepfake to trigger a catastrophic loss.
- Advanced AI Filtering: We use defensive AI tools that analyze incoming video and audio for the digital “fingerprints” of manipulation that the human eye can’t see.
Conclusion: Verification is the New Security
In the era of deepfakes, the old rules of “Cybersecurity Awareness” are no longer enough. You can’t just “check the link” when the person on the other side of the screen looks like your business partner.
Krypto IT is here to help you navigate this complex new landscape. We provide the technical shields and the strategic processes that keep your Houston business safe from even the most sophisticated AI-driven threats.
Are you ready to modernize your defenses against the new face of BEC? Contact Krypto IT today for a “Deepfake Defense Audit” and let’s ensure your team is prepared for 2026.