The True Cost of Downtime: A Number SMBs Can’t Afford to Ignore
October 23, 2025
Beyond Passwords: The Power of Identity and Access Management (IAM)
October 27, 2025For many small to medium-sized business (SMB) owners in Houston, a cyberattack feels like an abstract concept—something that happens to giant corporations, not their local business. This perception is a dangerous myth. In reality, SMBs are frequently targeted, not because they have vast resources, but because they are often the path of least resistance.
Cybercriminals are looking for easy wins. They aren’t trying to breach NASA; they’re trying to breach the busy, under-resourced business that hasn’t invested in professional cybersecurity.
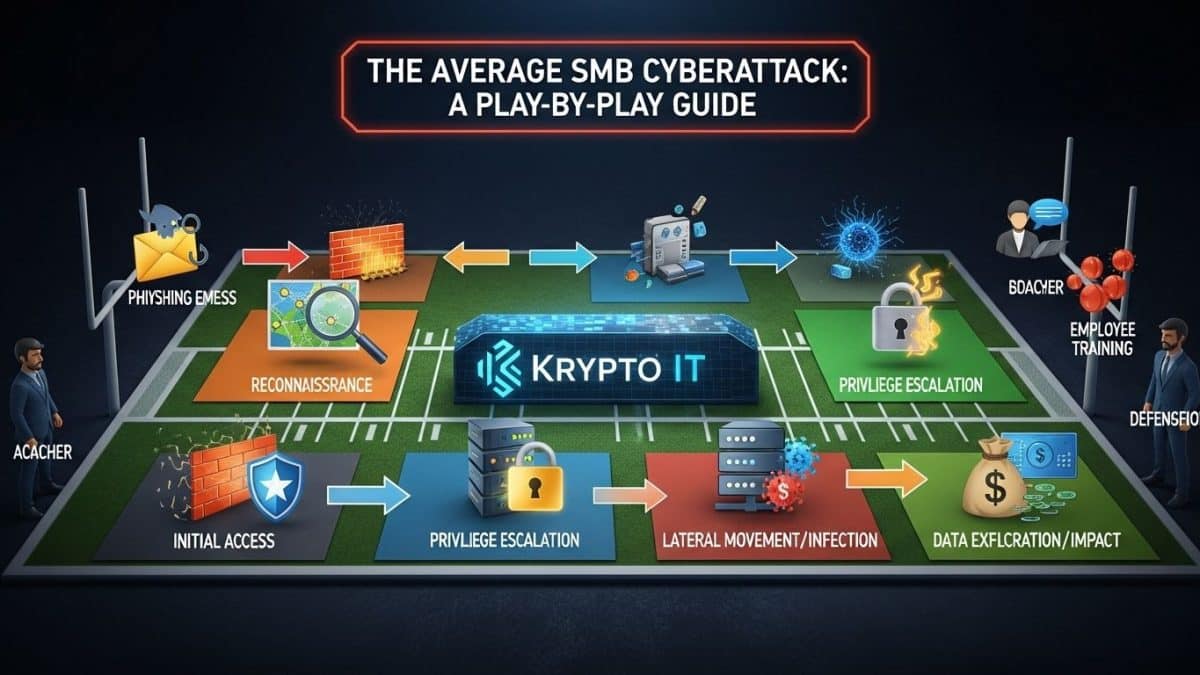
At Krypto IT, we’ve seen this play out countless times. Understanding the common sequence of an SMB cyberattack isn’t about fear-mongering; it’s about empowerment. Knowing the steps makes you realize where proactive defenses from an MSP become absolutely critical.
Act 1: The Initial Compromise (The Foot in the Door)
This is the subtle beginning, often unnoticed for days or weeks.
- The Phishing Expedition: The attack almost always starts with a social engineering tactic. A convincing email arrives, seemingly from a known vendor, a bank, or even the CEO (phishing or spear-phishing). It might contain a malicious link or an infected attachment.
- SMB Vulnerability: Employees are often under-trained on modern phishing techniques, especially those powered by AI that are grammatically perfect and highly personalized. In a busy office, one quick click is all it takes.
- Credential Theft / Malware Download: Once the link is clicked or the attachment opened, one of two things usually happens:
- Option A (Credential Theft): The user is redirected to a fake login page (e.g., a Microsoft 365 lookalike) where they unwittingly enter their legitimate username and password. Now the criminal has valid credentials.
- Option B (Malware Drop): Malicious software (like a trojan or keylogger) is silently downloaded onto the employee’s computer. It then begins to “call home” to the attacker’s server.
- SMB Vulnerability: Lack of Multi-Factor Authentication (MFA) means stolen credentials grant instant access. Outdated antivirus (or no EDR) misses the initial malware download.
Act 2: Reconnaissance and Lateral Movement (The Silent Invasion)
With a foot in the door, the attacker doesn’t immediately launch ransomware. They are looking for maximum impact.
- Gaining a Foothold: Using the stolen credentials or the malware on the compromised device, the attacker gains initial access. They often install legitimate-looking remote access tools to ensure persistent access, even if the user changes their password.
- Internal Mapping: The attacker then spends days, even weeks, exploring your network. They want to know:
- Which servers hold your most critical data? (e.g., customer databases, financial records, intellectual property).
- Where are your backups stored, and are they connected to the network?
- Who has administrative access, and can they get those credentials?
- SMB Vulnerability: Lack of 24/7 network monitoring (like SIEM or EDR) means these internal movements go completely undetected. Over-privileged user accounts give attackers easy access to sensitive areas.
- Lateral Movement: The attacker moves from the initial compromised workstation to more critical servers and systems, often escalating their privileges along the way. They might disable security software or create new admin accounts.
- SMB Vulnerability: Flat networks without proper segmentation allow easy movement. A lack of regular patch management means attackers can exploit known vulnerabilities to move between systems.
Act 3: Exfiltration and Execution (The Devastation)
This is the point of no return—when the attacker makes their move.
- Data Exfiltration: Before locking your systems, the criminal often steals a copy of your most valuable data. This gives them leverage: pay the ransom, or we release your sensitive information. This is known as “double extortion.”
- Ransomware Deployment: The attacker then unleashes the ransomware. This encrypts all your critical files and systems, making them inaccessible. A ransom note appears, demanding payment (often in cryptocurrency) for the decryption key.
- Impact: Your entire business grinds to a halt. Employees can’t access files, emails are down, the website is offline, and payment processing stops.
- SMB Vulnerability: Inadequate or connected backups mean you can’t restore quickly without paying. No Incident Response Plan leads to panic and delays, increasing the cost of downtime.
Why You Need a Pro: Krypto IT’s Proactive Defense
Trying to defend against this multi-stage attack with an internal “IT Guy” or reactive fixes is like bringing a knife to a gunfight. You need a proactive, layered defense that a professional MSP provides:
- Pre-Emptive Measures: We implement MFA, advanced email filtering, and robust EDR to stop the initial compromise.
- Active Monitoring: Our 24/7 SIEM/SOC detects the reconnaissance and lateral movement before the attacker reaches your critical data.
- Bulletproof Backups: We ensure secure, off-site, and tested backups (following the 3-2-1 rule) so you never have to pay a ransom.
- Rapid Response: If an incident occurs, our Incident Response Plan is activated immediately, containing the threat and minimizing downtime.
- Employee Training: We turn your employees into a strong first line of defense against social engineering.
Krypto IT understands the playbook of the average SMB cyberattack. Don’t wait for your business to become the next play-by-play example.
Contact Krypto IT today for a free cybersecurity assessment and build a defense that outsmarts the attackers.