Securing the Shop Floor: Mobile Device Security in Manufact
April 26, 2025
Incident Response Planning for Manufacturing
April 29, 2025Containing the Uncontainable: Why Network Segmentation Matters for Manufacturers
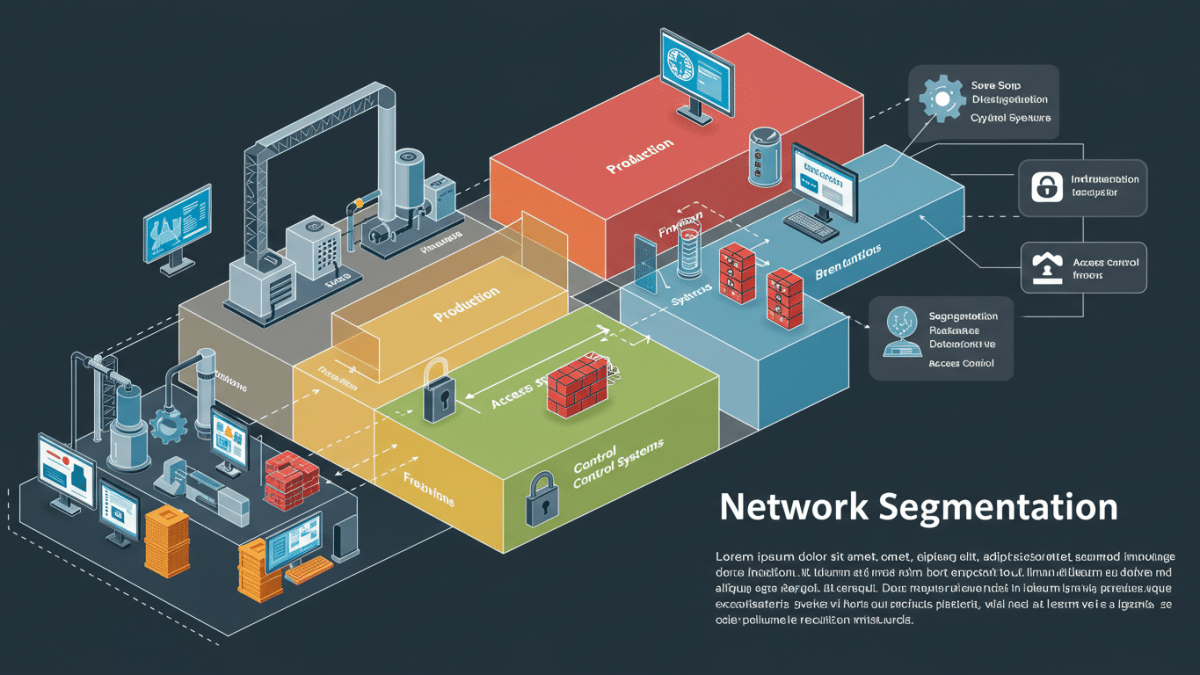
In today’s interconnected world, manufacturers face an ever-evolving landscape of cyber threats. From ransomware attacks that halt production lines to data breaches that compromise sensitive intellectual property, the potential for significant financial and operational damage is immense. While robust perimeter security measures are crucial, a layered defense strategy is essential. One of the most effective techniques in this arsenal is network segmentation.
Think of your manufacturing network as a large building with many rooms. Without internal walls and doors, if a burglar breaks in through one window, they have free access to the entire building. Network segmentation acts like those internal walls and locked doors in your digital infrastructure. It divides your network into distinct, isolated segments, controlling the traffic flow between them. This means that if a cybercriminal manages to breach one part of your network, their movement and potential damage can be significantly contained, preventing them from accessing critical operational technology (OT) systems, sensitive data, or other vital areas.
Demystifying the Technicalities: How Segmentation Works
At its core, network segmentation involves creating logical divisions within your network using various technologies and techniques. Here are some key concepts explained simply:
- Virtual Local Area Networks (VLANs):
Imagine creating separate virtual networks within your existing physical network infrastructure. VLANs allow you to group devices logically, even if they are physically connected to the same switches. For example, you could have a VLAN for your office computers, another for your engineering workstations, and a separate one for your industrial control systems (ICS). Traffic between these VLANs is restricted unless explicitly allowed.
- Firewalls:
These act as gatekeepers between network segments, enforcing security policies and controlling which traffic can pass through. Modern firewalls offer advanced features like stateful packet inspection and application-level filtering, providing granular control over network communications.
- Access Control Lists (ACLs):
Think of ACLs as rulebooks applied to network devices like routers and switches. They define specific conditions (e.g., source and destination IP addresses, port numbers) that determine whether network traffic should be permitted or denied.
- Microsegmentation:
This takes segmentation to a more granular level, isolating individual workloads or applications. In a manufacturing environment, this could mean segmenting individual machines or production cells, providing even finer-grained control and limiting the blast radius of an attack.
The Tangible Benefits for Manufacturing
Implementing network segmentation offers a wealth of advantages specifically tailored to the needs and challenges of manufacturing businesses:
- Enhanced Security and Breach Containment:
As highlighted earlier, this is the primary benefit. By limiting the lateral movement of attackers, segmentation significantly reduces the potential impact of a successful cyber intrusion. An attacker who breaches the guest Wi-Fi network, for instance, won’t be able to directly access critical production control systems.
- Improved Operational Technology (OT) Security:
Manufacturing environments heavily rely on OT systems like PLCs, SCADA systems, and industrial robots. These systems are often more vulnerable and can have severe real-world consequences if compromised. Segmenting the OT network from the IT network is crucial to protect these critical assets from cyberattacks originating in less secure areas.
- Reduced Downtime and Production Losses:
A successful cyberattack can bring manufacturing operations to a standstill, resulting in significant financial losses due to halted production, missed deadlines, and reputational damage. By containing breaches, network segmentation minimizes downtime and ensures business continuity.
- Simplified Compliance and Auditing:
Many regulatory frameworks, such as GDPR, HIPAA (if applicable to healthcare manufacturing), and industry-specific standards, require organizations to implement adequate security measures. Network segmentation can help manufacturers meet these compliance requirements by demonstrating clear control over data access and network security. It also simplifies auditing processes by providing a well-defined and controlled network environment.
- Optimized Network Performance:
By isolating network traffic, segmentation can reduce congestion and improve overall network performance. This is particularly beneficial in industrial environments with a high volume of data being transmitted between devices and systems.
Ready to Fortify Your Manufacturing Network?
Don’t wait for a cyber incident to expose the vulnerabilities in your network. Proactive implementation of network segmentation is a critical step in building a resilient and secure manufacturing environment.
Contact Krypto IT today for a free, no-obligation consultation. Our cybersecurity experts understand the unique challenges faced by small to medium-sized manufacturers in Houston, Texas, and we can help you develop a tailored network segmentation strategy to protect your valuable assets and ensure business continuity.
#NetworkSegmentation #ManufacturingSecurity #OTSecurity #CybersecurityForSMB #HoustonTech #KryptoIT #FreeConsultation