The Principle of Least Privilege: Giving Employees Only the Keys They Need to Do Their Job
November 7, 2025
Disabling SMBv1: The Simple Setting Change That Blocks a Major Cyber Threat
November 9, 2025By the Team at Krypto IT | Cybersecurity Experts Serving Houston SMBs
In the world of small and medium-sized businesses (SMBs), speed and collaboration are essential. But when it comes to your IT network, having an open, unified structure—a single, sprawling digital room—is one of the most dangerous risks you can take. If a criminal gets through the front door, they have immediate, unrestricted access to everything.
This risk is why Network Segmentation isn’t just a best practice for Fortune 500 companies; it is a critical, affordable defensive strategy that every Houston-area SMB should implement. Think of it not as building a complex maze, but as building internal, locked doors to contain a crisis.
The Danger of the “Flat” Network
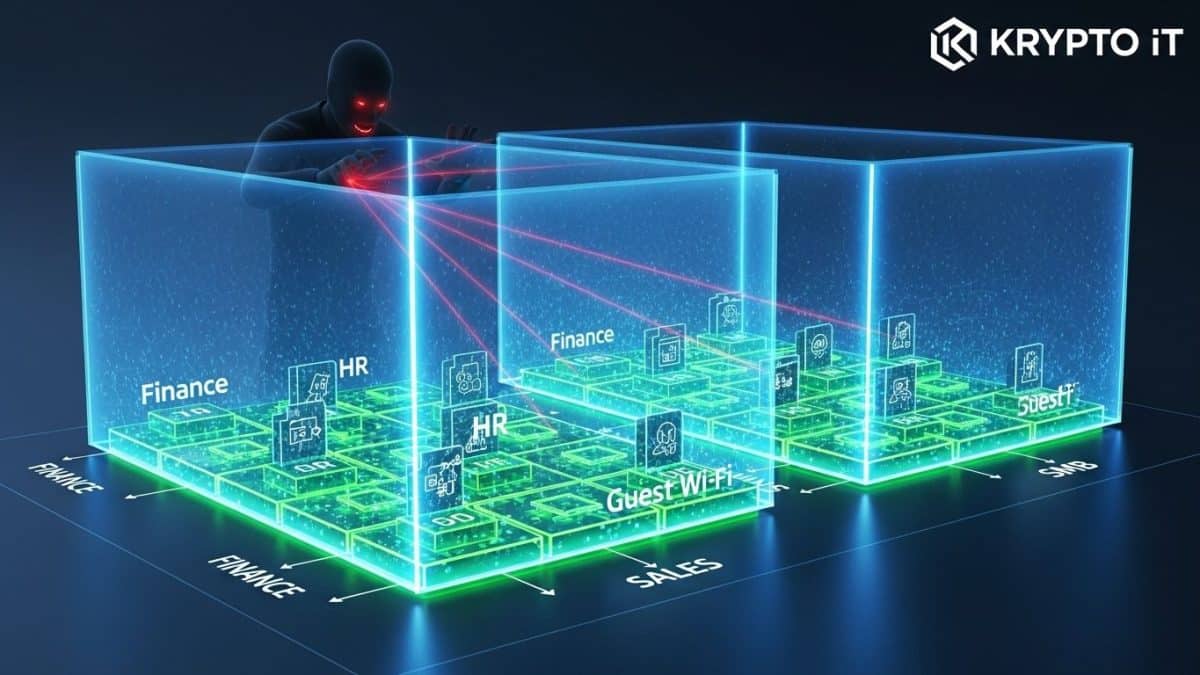
Imagine your office is one giant, open-plan floor. The server room, the finance office, the receptionist desk, and the guest lounge are all connected with no interior walls. If a fire starts in the kitchenette, it can instantly spread and consume the entire floor.
That’s exactly how a traditional, “flat” network works. A single vulnerability—a phishing email opened by a marketing intern, a weak password on a remote printer, or an unpatched legacy system—provides a single point of failure. Once a hacker gains access through that single hole, they are inside the main network and can immediately move laterally to access the most critical assets:
- Client databases (PII).
- Financial records and banking credentials.
- HR files and sensitive payroll data.
- Proprietary blueprints or intellectual property.
In a flat network, there are no internal barriers to slow down ransomware or block a determined attacker.
What Exactly is Network Segmentation? (The Security Building Analogy)
Network segmentation is the practice of dividing a large, monolithic network into smaller, isolated subnetworks, or “segments.”
To understand it simply, think of your office building again:
- The Main Firewall is the security guard at the front entrance, checking IDs.
- Network Segmentation is the key card access, coded doors, and secure vaults inside the building.
If a guest (a temporary, unsecure device) gets past the front desk, they can only access the Wi-Fi segment, not the server room (the Finance segment). If a virus infects a workstation in the Marketing segment, the infection is contained and cannot hop over to the Legal segment.
Segmentation uses internal firewalls, Virtual Local Area Networks (VLANs), and sophisticated access controls to define who (or what) can talk to whom.
Three Critical Security Wins for Segmented SMBs
For small to medium-sized businesses, the benefits of implementing digital walls with the help of Krypto IT are immediate and dramatic:
1. Damage Containment: Stop the Spread
This is the number one reason to segment. In the event of a breach, time is everything. A properly segmented network means a ransomware attack that hits one device is isolated to that specific subnet. Instead of facing a company-wide shutdown and a six-figure cleanup bill, Krypto IT can focus on quarantining the affected segment, often allowing the rest of your business operations to continue uninterrupted. Containment drastically reduces recovery time and cost.
2. Regulatory Compliance is Easier
If your SMB handles sensitive information—such as customer payment details (PCI DSS) or private health information (HIPAA)—segmentation is often a requirement or a massive compliance advantage. By placing systems that process sensitive data into their own isolated, hyper-secure network segments, you limit the scope of your compliance audits and dramatically reduce the risk of massive regulatory fines.
3. Protecting the “Crown Jewels”
Not all data is created equal. Your Finance and HR departments deal with the most valuable and sensitive information. With segmentation, we can establish a high-security zone just for these critical assets, providing them with tighter monitoring and stricter access controls than, say, the marketing team’s general file sharing area. This targeted defense ensures your most sensitive assets are never sitting on the same easily accessible network as the guest Wi-Fi or a smart coffee machine.
Practical Segmentation in the Real World
Segmentation doesn’t have to be overwhelming. Krypto IT specializes in creating manageable, practical segments tailored to the needs of Houston SMBs:
- Guest Network Isolation: Absolutely essential. Guests and their devices should never, under any circumstances, touch your primary business network.
- IoT & Operations: Separate networks for all non-traditional devices like security cameras, smart thermostats, printers, and manufacturing equipment. These devices are notoriously insecure and must be walled off.
- Administrative Separation: Isolating servers, backup systems, and IT management tools into a segment only accessible by verified IT professionals (like the Krypto IT team) and nothing else.
- Departmental Separation: Creating internal segments for Finance, HR, and Sales ensures that if one department falls victim to an attack, the breach cannot immediately spread to another.
Why Partner with Krypto IT?
Implementing network segmentation is complex. It requires deep expertise in network architecture, VLAN configuration, internal firewall rules, and access control lists. A mistake can lead to connectivity problems, system downtime, or, worse, a false sense of security.
The Krypto IT team handles this complexity for you. We design, deploy, and continuously manage your segmented network, ensuring that your digital walls are strong, correctly configured, and consistently maintained to meet the latest threat landscapes. We monitor the traffic between your segments 24/7, catching the moment a threat tries to move from the guest network to your financial servers.
Don’t leave your entire business exposed because of a single vulnerability. Invest in digital architecture that protects your future.
Ready to stop a small incident from becoming a total disaster?
Contact Krypto IT today for a complimentary network security assessment. We’ll show you exactly where your flat network risks lie and how we can implement a segmented, layered defense to protect your business’s critical data.