Inventory Your Assets: Knowing What You Have is the First Step to Protecting It
November 18, 2025
Creating Your Simple Security Policy: Setting the Digital Rules of the Road
November 21, 2025By the Team at Krypto IT | Cybersecurity Experts Serving Houston SMBs
For the small to medium-sized business (SMB) owner, cyber insurance has become an almost non-negotiable expense—a vital financial safety net in a world dominated by ransomware and data breaches. You insure your office space, your vehicles, and your inventory. Shouldn’t you insure your most valuable asset: your data?
The answer is a resounding yes. However, cyber insurance is not like standard business liability insurance. It’s complex, highly specific, and often contains traps that can lead to a denied claim if your business hasn’t maintained specific security controls.
At Krypto IT, we believe that understanding your cyber policy is just as important as having one. Here is a clear guide on what cyber insurance is designed to cover, what it often excludes, and why your SMB needs it now.
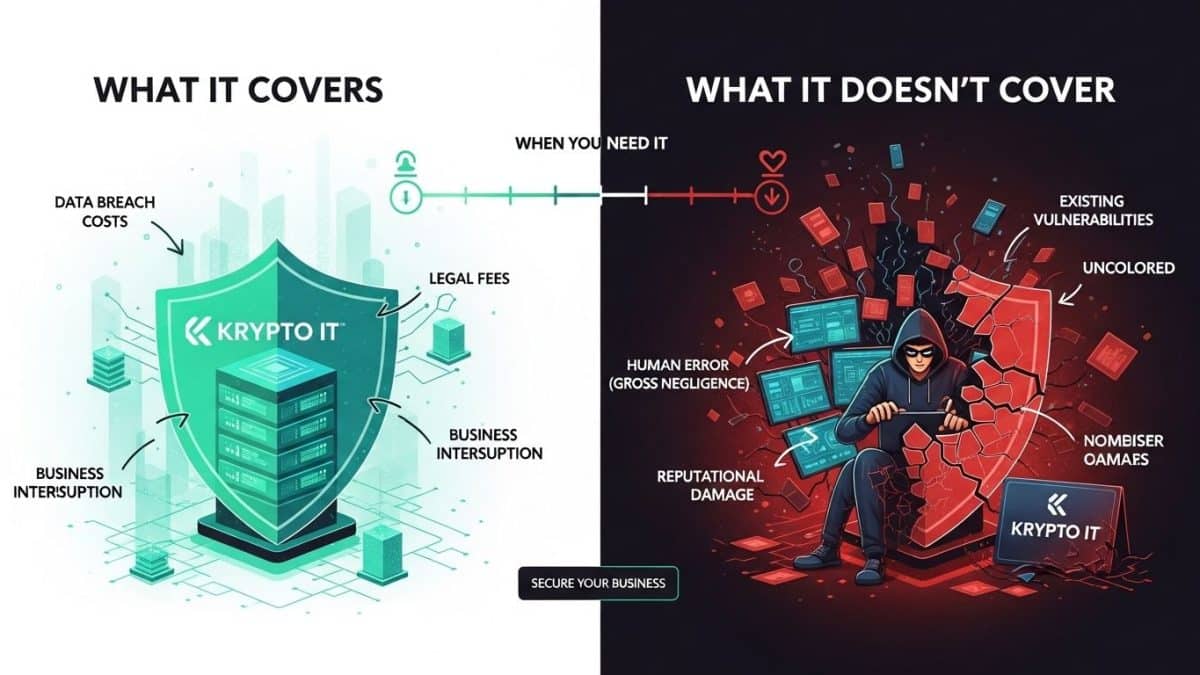
What Cyber Insurance Is Designed to Cover (The Financial Lifeline)
Cyber insurance is designed to cover the specific costs associated with a security incident that traditional policies (like property insurance) won’t touch. This coverage usually falls into two categories: First-Party costs (your costs) and Third-Party costs (costs related to others).
First-Party Coverage (Costs You Incur Directly)
These are the immediate expenses necessary to recover and contain the breach.
- Incident Response and Forensics: The cost of hiring specialized forensic IT teams (like those often partnered with Krypto IT) to investigate the breach, determine the cause, and identify the scope of the damage. This is often the largest immediate expense.
- Ransomware and Extortion: Coverage for the actual ransom payment (if negotiation and payment are necessary) and the cost of hiring experts to handle the negotiation and cryptocurrency transfer.
- Business Interruption: Reimburses you for lost income during the period when your business operations are fully or partially shut down due to the cyber incident.
- Data Restoration: The costs associated with restoring your damaged or lost data, systems, and software, often utilizing your verified backups.
Third-Party Coverage (Costs Related to Others)
These cover the costs resulting from claims or lawsuits filed against your business by customers or partners due to the breach.
- Legal Defense and Liability: Coverage for the legal fees and settlements resulting from lawsuits filed by customers, vendors, or shareholders claiming damages from the breach.
- Regulatory Fines: Coverage for fines and penalties imposed by regulatory bodies (e.g., state attorneys general, HIPAA) for failing to protect customer data.
- Notification Costs: The legally mandated cost of notifying all affected customers that their data was compromised, which often includes setting up call centers or providing credit monitoring services.
What Cyber Insurance Often Excludes (The Gaps)
This is where policies become tricky, and where Krypto IT provides crucial value. Many claims are denied because the SMB failed to meet specific security prerequisites or because the incident falls under a common exclusion.
1. Failure to Meet Minimum Security Standards
Policies are contingent on you maintaining a reasonable level of security. If your policy mandates it and you fail to:
- Enforce Multi-Factor Authentication (MFA) for all remote access and email accounts.
- Maintain Tested, Off-site Backups (the 3-2-1 Rule).
- Apply Software Patches to critical operating systems in a timely manner. The insurer can deny your claim due to your failure to maintain “due care.”
2. Social Engineering and Voluntary Fund Transfers
Many standard cyber policies specifically exclude losses resulting from Social Engineering Fraud or Voluntary Funds Transfer—for instance, an employee being tricked by a Business Email Compromise (BEC) scam into wiring money to a criminal. If your policy does not have a specific Social Engineering Rider added, this common type of attack may not be covered.
3. Cost of “Improving” Your Systems
Insurance pays for the cost of returning your systems to their pre-breach state, not for upgrading them. If the forensic team recommends you purchase a new next-gen firewall or deploy a full EDR system, the policy typically won’t cover those upgrades.
When Does Your SMB Need Cyber Insurance? (The Answer is Now)
If your SMB meets any of the following criteria, you need cyber insurance, and you need it now:
- You Accept Credit Cards: Your compliance with PCI DSS makes you a mandatory target, and you need coverage for the resulting fines and transactional disruption.
- You Store PII/PHI: If you store employee or customer Personally Identifiable Information (PII) or Protected Health Information (PHI), a breach triggers massive legal, regulatory, and notification costs.
- You Rely on Email/Cloud for Operations: Since BEC and Ransomware are the top threats, and both target email and cloud access, your financial exposure is immediate and critical.
The Krypto IT Partnership: Validating Your Policy
Cyber insurance is a financial tool, but an MSP is your technical validation tool. Krypto IT works with your broker to ensure your policy is valid by:
- Compliance Assurance: We manage and document all the required minimum security controls, such as enforcing MFA across the network and ensuring your 3-2-1 backup rule is always active and tested.
- Risk Reduction: By implementing EDR and providing 24/7 network monitoring, we significantly reduce the likelihood of an attack reaching the “claim” stage, which can lead to better renewal terms.
- Incident Facilitation: If a claim is filed, we provide the necessary technical logs and forensic data to the insurer’s team, accelerating the validation process and speeding up your recovery.
Don’t buy a false sense of security. Buy a policy, and let Krypto IT ensure your infrastructure meets the standard required for that policy to pay out.
Ready to ensure your security posture aligns perfectly with your cyber insurance policy?
Contact Krypto IT today for a complimentary security compliance check.